The short answer is: not about this patch. The effects of CVE-2022-3786 and CVE-2022-3602 on ICS, IoT, and IoMT devices are negligible. But the long answer is more complex than this.
But first things first:
OpenSSL released an announcement on October 25th, 2022 that their upcoming release of OpenSSL 3.0.7 will contain patches of critical vulnerabilities, giving a head-start to affected organizations to schedule maintenance windows and to prepare for rapid patching of affected systems.
Further investigations into CVE-2022-3602, a 4-byte buffer overflow when parsing email addresses containing puny code in X.509 certificates, in the week preceding the release did not confirm initial assumptions about the likelihood of exploitability in common configurations. Thus, the severity was lowered to “high” as common stack layouts and modern stack overflow protections reduce the impact of the issue.
The two vulnerabilities patched in OpenSSL 3.0.7 affect the OpenSSL 3 branch, versions 3.0.0 through 3.0.6.
Having analyzed tens of thousands of firmware images of connected devices, and having automatically generated the software bill of materials (SBOM) for these devices, we were naturally interested about the effects this vulnerability would have on the security of these devices. OpenSSL is a common library, also used in connected devices to support encrypted communication. But OpenSSL 3 is not.
OpenSSL 3 was released just over a year ago, on September 7, 2021. Any firmware images released before this date, therefore cannot contain OpenSSL 3, and therefore cannot be affected by these vulnerabilities (but will likely be affected by many other vulnerabilities). We have investigated the distribution of OpenSSL versions and OpenSSL 3 is used by less than 0.1% of devices:
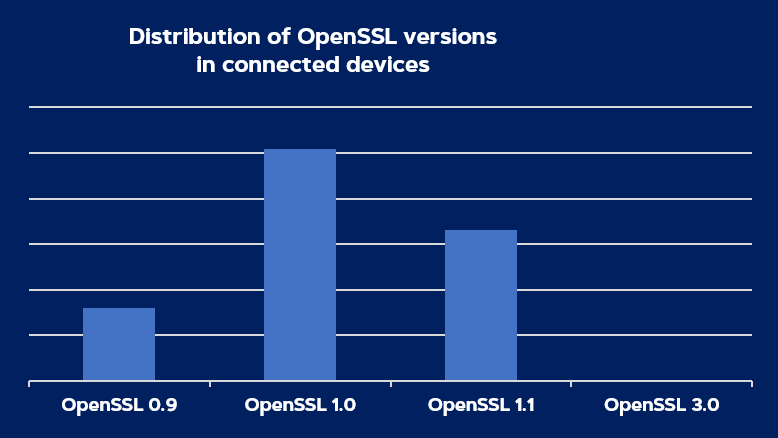
While device vendors and operators of connected devices don’t have to wake up at night for OpenSSL 3 related security issues, this investigation uncovered other worrying facts:
But why is this?
Aside from a general difficulty to keep dependencies and systems up to date, where vendors of connected devices are no exceptions, popular Linux distributions play an important role too:
For OpenSSL, it is common to be statically linked into other products. Vendors relying on 3rd party SDKs or libraries who have OpenSSL included may not even be aware of this fact.
In the ICS and IoT world, we may have been lucky this time, not to be affected by CVE-2022-3786 and CVE-2022-3602. But with LTS of OpenSSL 1.1.1 ending in less than a year on September 11th, 2023, this should serve as a wakeup call that we need to get our dependencies in order and keep our software bill of material (SBOM) up to date.
A first step to tackle this issue is to gain visibility into your and your supply-chain’s dependencies. We’re ready to help!